A new cyber attack is hijacking router’s DNS settings so that web browsers display alerts for a fake COVID-19 information app from the World Health Organization that is the Oski information-stealing malware.
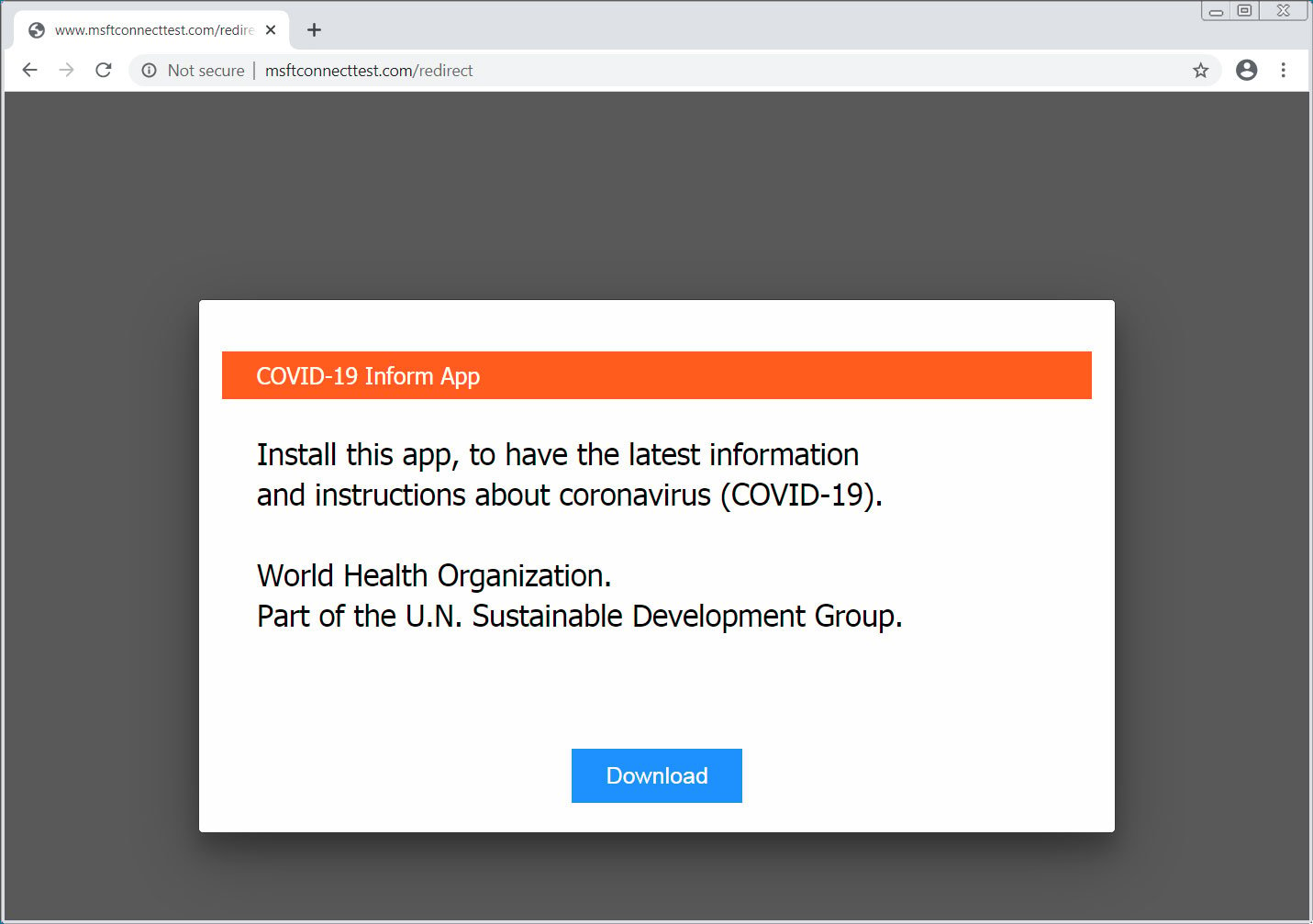
For the past five days, people have been reporting their web browser would open on its own and display a message prompting them to download a ‘COVID-19 Inform App’ that was allegedly from the World Health Organization (WHO).
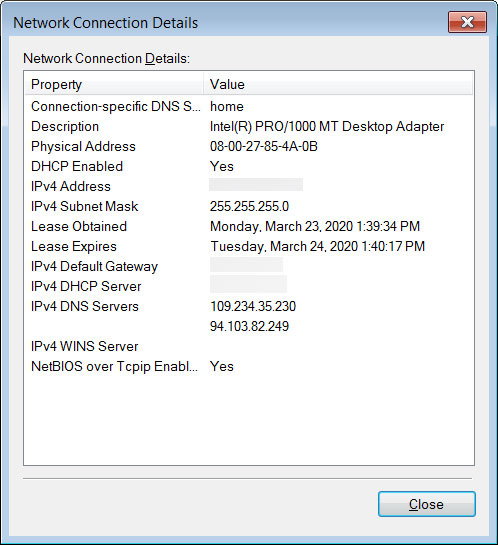
After further research, it was determined that these alerts were being caused by an attack that changed the DNS servers configured on their home Linksys, and possibly D-Link [1], routers to use DNS servers operated by the attackers.
As most computers use the IP address and DNS information provided by their router, the malicious DNS servers were redirecting victims to malicious content under the attacker’s control.
Hijack Windows NCSI active probes
At this time, it is not known how the attackers are gaining access to the routers to change their DNS configuration, but some users state that they had remote access to the router enabled with a weak admin password.
What you should do if affected by this attack
If your browser is randomly opening to a page promoting a COVID-19 information app, then you need to login to your router and make sure you configure it to automatically receive its DNS servers from your ISP.
As every router has a different way of configuring DNS servers, it is not possible to give a specific method on how to do this.
In general, you will want to follow these steps:
- Login to your router
- Find the DNS settings and make sure there are no servers, especially 109.234.35.230 and 94.103.82.249, manually configured. If they are, set the DNS servers setting to ‘Automatic’ or ISP assigned.
- Then save your configuration.
You should now be able to reboot your mobile devices, game consoles, and computers so that they use the correct DNS settings from your ISP.
As people are reporting that they think their settings were changed because of a weak password and that remote administration was enabled, it is important to change your password to something stronger and to disable remote administration on the router.
Finally, if you downloaded and installed the COVID-19 app, you should immediately perform a scan on your computer for malware.
Once clean, you should change all of the passwords for sites whose credentials are saved in your browser and you should change the passwords for any site that you visited since being infected.
When resetting your passwords, be sure to use a unique password at every site.